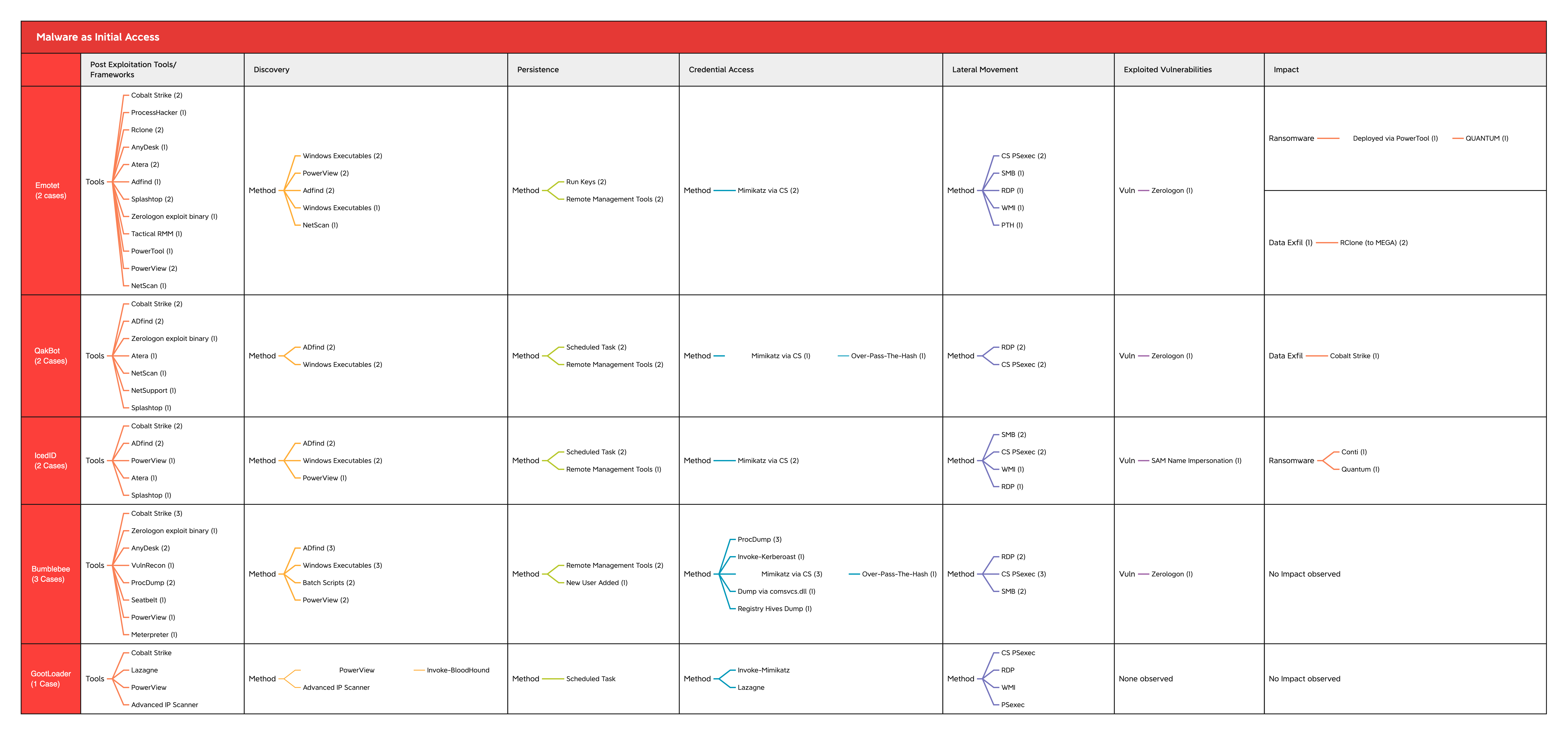
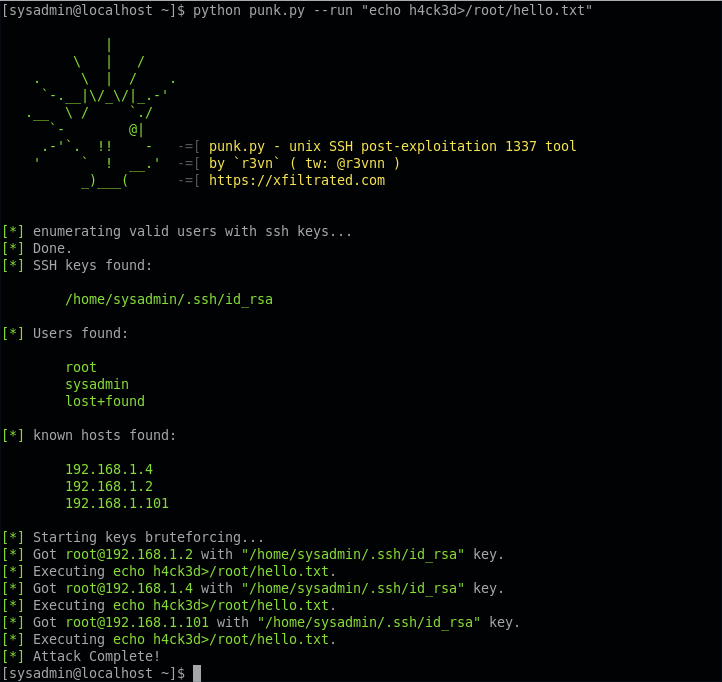
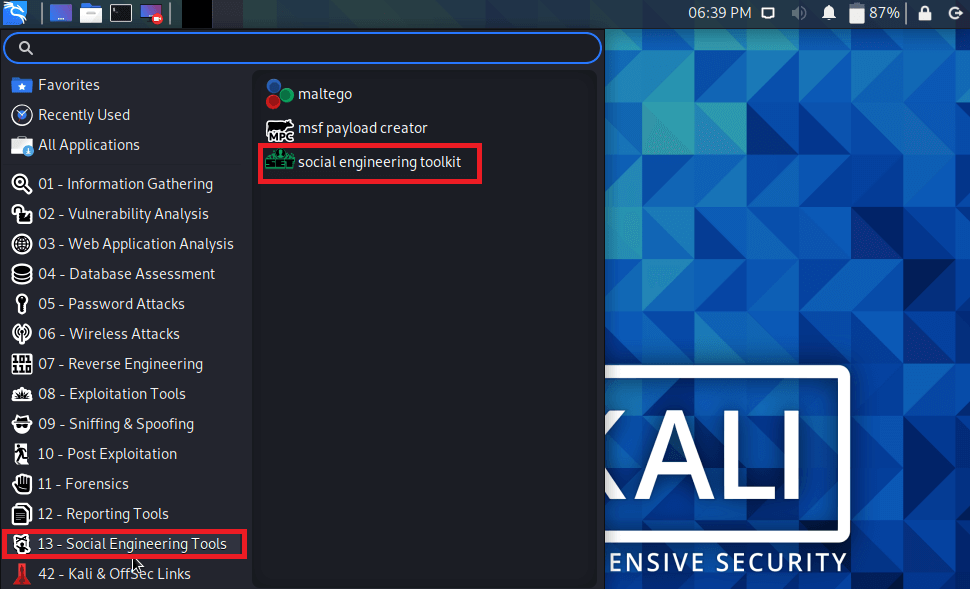
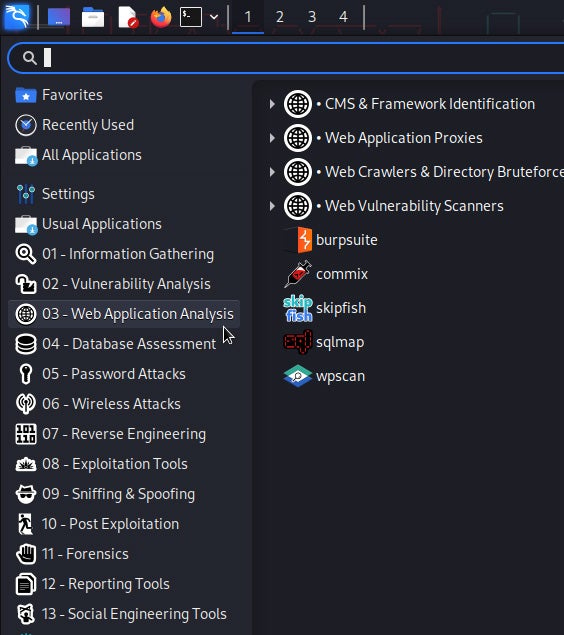
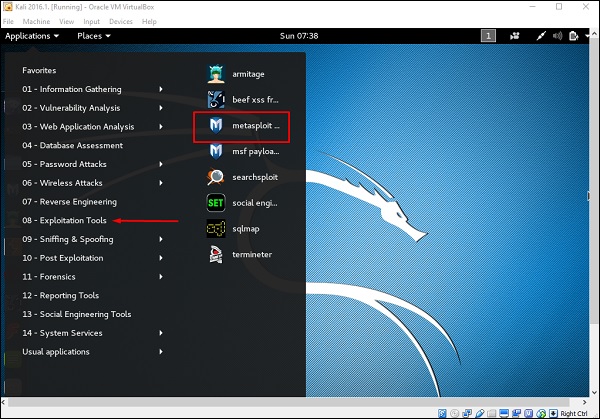
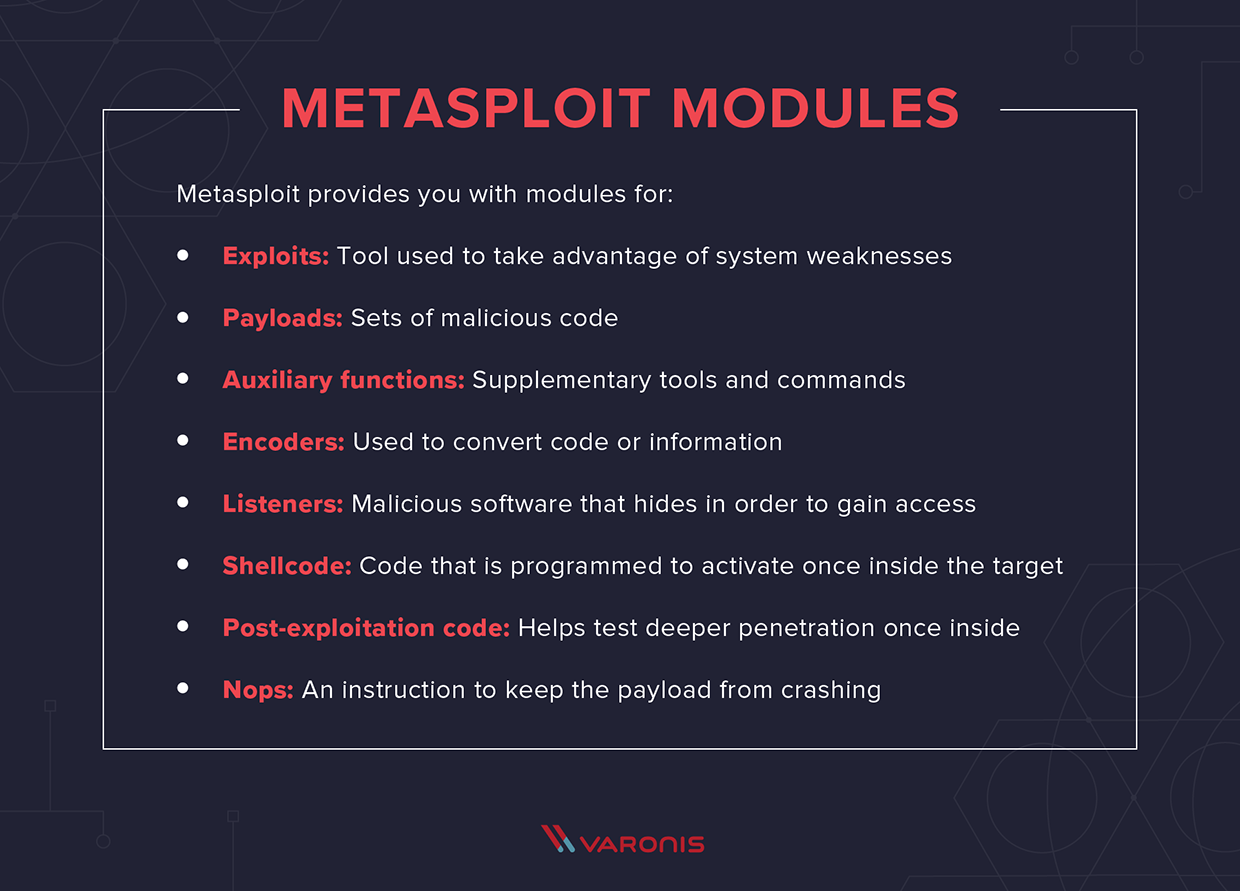
Post-Exploitation Techniques: Maintaining Access, Escalating Privileges, Gathering Credentials, Covering Tracks | Black Hat Ethical Hacking

Evasor - A Tool To Be Used In Post Exploitation Phase For Blue And Red Teams To Bypass APPLICATIONCONTROL Policies


![Using RedRabbit's Best Pentesting & Post-Exploitation Tools on Windows [Tutorial] - YouTube Using RedRabbit's Best Pentesting & Post-Exploitation Tools on Windows [Tutorial] - YouTube](https://i.ytimg.com/vi/nbZ0xs6LKrE/hq720.jpg?sqp=-oaymwEhCK4FEIIDSFryq4qpAxMIARUAAAAAGAElAADIQj0AgKJD&rs=AOn4CLBYQSMrcZgc3s9W7LKiaTn6lmfvTw)